Repairing a Nikon D80 with ERR message
Publicado el 4th Diciembre, 2021 por KaRMaN. Archivado en Cacharros, Electrónica, Hardware.Leido 29,964 veces. Comments Off
Initially introduced at $999 body only this was a prosumer camera back in 2006. Later years and up today photography comunity members started to report a ERR message in their cameras top display (in the shutter speed field). This error is commonly associated to the mechanical parts of the camera (shutter, diaphragm and mirror) being not properly in sync.
I have already fixed 3 cameras with these flaws. These cameras where brougth to me as for parts/teardowns so I decided to publish a small guideline on how to fix them.
Seems that this specific model of Nikon had two major flawn that made the mechanics out of sync. Maybe the fault comes from the design, maybe comes from quality control. The flawns are:
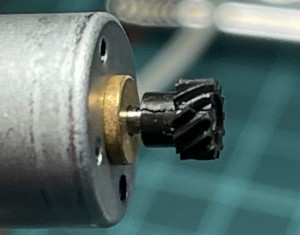
Main motor pinion gets broken. This makes the pinion too loose so the motor spins without transmiting it’s force to the mecanism and rotating in void. The main electronics detects no action in it’s sensors despite givin the command to spin the motor, hence produces the ERR message. This is fixable by carefully removing the pinion, putting a smal drop of SuperGlue in the motors shaft tip then pushing back the pinion.
Mechanics encoder loses one brush fixing. The mechanic rotatory enconder is the electronics main sensor of the mecanics position and travel. It’s made of a gear that has a fixed brushes against a PCB board where makes it’s contact. The brushes are fixed by a plastic welding that brokes with passing time. The brushes then missaling or makes no contact at all. Electronics loses perception of the mechanics travel and position and then drops the fatal ERR message. This can be fixed with a small drop of superglue in the affected/broken plastic fixing (in this photo, the right side one).
I recommend to let dry the superglue at least 1 hour before trying the fix. You can start assembling the camera inmediatly but is best for all to let it totally dry before inserting a charged battery to try it out.
Any of these flaws renders the camera unusable. Fortunally both flaws are relative easy to fix, but both requires a lot of careful dissasembly to be able to get to the afected parts. I recommend to follow the help this Nikon D80 service manual and use a welder when the disassembly requires to unsolder some wires.